We now have an official Red Hat Security Blog, and you'll find all my future reports and discussions about security metrics there. In the meantime here are a few already published articles:
- How
Red Hat rates JBoss security flaws
- CWE
Vulnerability Assessment Report
- Welcome to the Red Hat Security Blog
A few weeks ago the 2011 update to the CWE/SANS Top 25 Most Dangerous Software Errors was published. As part of our contribution to this update we analysed the most severe vulnerabilities that affected Red Hat since the last update and mapped each one to the appropriate Common Weakness Enumeration (CWE) type.
The table below lists all vulnerabilities which have a CVSS score of 7 or more ('high'), that we fixed in any product during calendar year 2010.
Most common CWE were:
- Buffer Copy without Checking Size of Input (CWE-120): 8 vulnerabilities.
- Race Condition (CWE-362): 5 vulnerabilities.
| CVE | CWE | 2011 top 25? | CVSS base score | Fixed in |
|---|---|---|---|---|
| CVE-2007-4567 | CWE-476 | no | 7.8 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2009-0778 | CWE-770 | no | 7.1 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2009-1385 | CWE-191 | no | 7.1 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2009-3080 | CWE-129 | no | 7.2 | Red Hat Enterprise Linux 3, 4, 5, MRG (kernel) |
| CVE-2009-3245 | CWE-252 | no | 7.6 | Red Hat Enterprise Linux 3, 4, 5 (openssl) |
| CVE-2009-3726 | CWE-476 | no | 7.2 | Red Hat Enterprise Linux 4, 5, MRG (kernel) |
| CVE-2009-4005 | CWE-127 | no | 7.1 | Red Hat Enterprise Linux 4 (kernel) |
| CVE-2009-4027 | CWE-362 | no | 7.8 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2009-4141 | CWE-416 | no | 7.2 | Red Hat Enterprise Linux 5, MRG (kernel) |
| CVE-2009-4212 | CWE-191 | no | 10.0 | Red Hat Enterprise Linux 3, 4, 5 (krb5) |
| CVE-2009-4272 | CWE-764 | no | 7.8 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2009-4273 | CWE-78 | yes | 7.9 | Red Hat Enterprise Linux 5 (systemtap) |
| CVE-2009-4537 | CWE-120 | yes | 7.1 | Red Hat Enterprise Linux 4, 5, MRG (kernel) |
| CVE-2009-4895 | CWE-362 | no | 7.2 | Red Hat Enterprise MRG (kernel) |
| CVE-2010-0008 | CWE-606 | no | 7.8 | Red Hat Enterprise Linux 4, 5 (kernel) |
| CVE-2010-0291 | CWE-822 | no | 7.2 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2010-0738 | CWE-424 | no | 7.5 | JBoss Enterprise Application Platform 4.2, 4.3 |
| CVE-2010-0741 | CWE-20 | no | 7.1 | Red Hat Enterprise Linux 5 (kvm) |
| CVE-2010-1084 | CWE-120 | yes | 7.2 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2010-1086 | CWE-20 | no | 7.8 | Red Hat Enterprise Linux 4, 5 (kernel) |
| CVE-2010-1087 | CWE-362 | no | 7.2 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2010-1166 | CWE-823 | no | 7.6 | Red Hat Enterprise Linux 5 (xorg-x11-server) |
| CVE-2010-1173 | CWE-120 * | yes | 7.1 | Red Hat Enterprise Linux 4, 5 (kernel) |
| CVE-2010-1188 | CWE-416 | no | 7.8 | Red Hat Enterprise Linux 3, 4, 5 (kernel) |
| CVE-2010-1436 | CWE-120 | yes | 7.2 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2010-1437 | CWE-362 | no | 7.2 | Red Hat Enterprise Linux 4, 5 (kernel) |
| CVE-2010-2063 | CWE-823 | no | 7.5 | Red Hat Enterprise Linux 3, 4, 5 (samba) |
| CVE-2010-2235 | CWE-77 | no | 7.1 | Red Hat Network Satellite Server 5.3 (cobbler) |
| CVE-2010-2240 | CWE-788 | no | 7.2 | Red Hat Enterprise Linux 3, 4, 5, MRG (kernel) |
| CVE-2010-2248 | CWE-682 | no | 7.1 | Red Hat Enterprise Linux 4, 5 (kernel) |
| CVE-2010-2492 | CWE-805 | no | 7.2 | Red Hat Enterprise Linux 5, 6 (kernel) |
| CVE-2010-2521 | CWE-805 | no | 8.3 | Red Hat Enterprise Linux 4, 5, MRG (kernel) |
| CVE-2010-2798 | CWE-476 | no | 7.2 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2010-2962 | CWE-823 | no | 7.2 | Red Hat Enterprise Linux 6, MRG (kernel) |
| CVE-2010-3069 | CWE-129 | no | 8.3 | Red Hat Enterprise Linux 3, 4, 5, 6 (samba) |
| CVE-2010-3081 | CWE-131 | yes | 7.2 | Red Hat Enterprise Linux 3, 4, 5, 6, MRG (kernel) |
| CVE-2010-3084 | CWE-120 | yes | 7.2 | Red Hat Enterprise Linux 6 (kernel) |
| CVE-2010-3301 | CWE-129 | no | 7.2 | Red Hat Enterprise Linux 6 (kernel) |
| CVE-2010-3302 | CWE-120 | yes | 7.1 | Red Hat Enterprise Linux 6 (openswan) |
| CVE-2010-3308 | CWE-120 | yes | 7.1 | Red Hat Enterprise Linux 6 (openswan) |
| CVE-2010-3432 | CWE-805 * | no | 7.8 | Red Hat Enterprise Linux 4, 5, 6, MRG (kernel) |
| CVE-2010-3705 | CWE-788 | no | 8.3 | Red Hat Enterprise Linux 6, MRG (kernel) |
| CVE-2010-3708 | CWE-77 | no | 7.5 | JBoss Enterprise Application Platform 4.3, SOA Platform 4.2 |
| CVE-2010-3752 | CWE-78 | yes | 7.1 | Red Hat Enterprise Linux 6 (openswan) |
| CVE-2010-3753 | CWE-78 | yes | 7.1 | Red Hat Enterprise Linux 6 (openswan) |
| CVE-2010-3847 | CWE-426 | no | 7.2 | Red Hat Enterprise Linux 5, 6 (glibc) |
| CVE-2010-3856 | CWE-426 | no | 7.2 | Red Hat Enterprise Linux 5, 6 (glibc) |
| CVE-2010-3864 | CWE-362 | no | 7.6 | Red Hat Enterprise Linux 6 (openssl) |
| CVE-2010-3904 | CWE-822 | no | 7.2 | Red Hat Enterprise Linux 5, 6 (kernel) |
| CVE-2010-4170 | CWE-88 | no | 7.2 | Red Hat Enterprise Linux 4, 5, 6 (systemtap) |
| CVE-2010-4179 | CWE-862 | yes | 7.5 | Red Hat Enterprise MRG (cumin) |
| CVE-2010-4344 | CWE-120 | yes | 7.5 | Red Hat Enterprise Linux 4, 5 (exim) |
* - in both these cases the outcome is not a buffer overflow as the possible overflow is detected and instead converted into an abort (DoS)
See also our 2010 analysis
The 2010 CWE/SANS Top 25 Most Dangerous Programming Errors was published today listing the most widespread issues that lead to software vulnerabilities.
During the creation and review of the list we spent some time to see how closely last years list matched the types of flaws we deal with at Red Hat. We first looked at all the issues that Red Hat fixed across our entire product portfolio in the 2009 calendar year and filtered out those that had the highest severity. All our 2009 vulnerabilities have CVSS scores, so we filtered on those that have a CVSS base score of 7.0 or above[1].
There were 22 vulnerabilities that matched, and we mapped each one to the most appropriate CWE. This gives us 11 flaw types which led to the most severe flaws affecting Red Hat in 2009:
| CWE | CWE Description | CWE/SANS top 25? | Number of Vulnerabilities |
|---|---|---|---|
| CWE-476 | NULL Pointer Dereference | No (on cusp) | 6 |
| CWE-120 | Buffer Copy without Checking Size of Input | Yes | 3 |
| CWE-129 | Improper Validation of Array Index | Yes | 3 |
| CWE-131 | Incorrect Calculation of Buffer Size | Yes | 3 |
| CWE-78 | OS Command Injection | Yes | 1 |
| CWE-285 | Improper Access Control (Authorization) | Yes | 1 |
| CWE-362 | Race Condition | Yes | 1 |
| CWE-330 | Use of Insufficiently Random Values | No (on cusp) | 1 |
| CWE-590 | Free of Memory not on the Heap | No | 1 |
| CWE-672 | Use of a Resource after Expiration or Release | No (on cusp) | 1 |
| CWE-772 | Missing Release of Resource after Effective Lifetime | No (on cusp) | 1 |
10 of the 11 CWE are mentioned in the 2010 CWE/SANS document, although 4 of them are on "the cusp" and didn't make it into the top 25.
This quick review shows us that 2009 was the year of the kernel NULL pointer dereference flaw, as they could allow local untrusted users to gain privileges, and several public exploits to do just that were released. For Red Hat, interactions with SELinux prevented them being able to be easily mitigated, until the end of the year when we provided updates. Now, in 2010, the upstream Linux kernel and many vendors ship with protections to prevent kernel NULL pointers leading to privilege escalation. So although 2009 was the year where CWE-476 mattered to Linux administrators, it didn't make the SANS/CWE top 25 as this flaw type should not lead to severe issues (as long as the protections remain sufficient).
Here is a breakdown with the complete data set to show the CVSS scores and packages affected:
| CVE | CWE | top 25? | CVSS base | Fixed in |
|---|---|---|---|---|
| CVE-2008-5182 | CWE-362 | Yes | 7.2 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2009-0065 | CWE-129 | Yes | 8.3 | Red Hat Enterprise Linux 4,5,MRG (kernel) |
| CVE-2009-0692 | CWE-120 | Yes | 8.3 | Red Hat Enterprise Linux 3,4 (dhcp) |
| CVE-2009-0778 | CWE-772 | No (on cusp) | 7.1 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2009-0846 | CWE-590 | No | 9.3 | Red Hat Enterprise Linux 2.1, 3 (krb5) [2] |
| CVE-2009-1185 | CWE-131 | Yes | 7.2 | Red Hat Enterprise Linux 5 (udev) |
| CVE-2009-1385 | CWE-129 | Yes | 7.1 | Red Hat Enterprise Linux 3,4,5,MRG (kernel) |
| CVE-2009-1439 | CWE-131 | Yes | 7.1 | Red Hat Enterprise Linux 4,5,MRG (kernel) |
| CVE-2009-1579 | CWE-78 | Yes | 7.5 | Red Hat Enterprise Linux 3,4,5 (squirrelmail) |
| CVE-2009-1633 | CWE-131 | Yes | 7.1 | Red Hat Enterprise Linux 4,5,MRG (kernel) |
| CVE-2009-2406 | CWE-120 | Yes | 7.2 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2009-2407 | CWE-120 | Yes | 7.2 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2009-2692 | CWE-476 | No (on cusp) | 7.2 | Red Hat Enterprise Linux 3,4,5,MRG (kernel) |
| CVE-2009-2694 | CWE-129 | Yes | 7.5 | Red Hat Enterprise Linux 3,4,5 (pidgin) |
| CVE-2009-2698 | CWE-476 | No (on cusp) | 7.2 | Red Hat Enterprise Linux 3,4,5 (kernel) |
| CVE-2009-2848 | CWE-672 | No (on cusp) | 7.2 | Red Hat Enterprise Linux 3,4,5,MRG (kernel) |
| CVE-2009-2908 | CWE-476 | No (on cusp) | 7.2 | Red Hat Enterprise Linux 5 (kernel) |
| CVE-2009-3238 | CWE-330 | No (on cusp) | 7.8 | Red Hat Enterprise Linux 4,5,MRG (kernel) |
| CVE-2009-3290 | CWE-285 | Yes | 7.2 | Red Hat Enterprise Linux 5 (kvm) |
| CVE-2009-3547 | CWE-476 | No (on cusp) | 7.2 | Red Hat Enterprise Linux 3,4,5,MRG (kernel) |
| CVE-2009-3620 | CWE-476 | No (on cusp) | 7.2 | Red Hat Enterprise Linux 4,5,MRG (kernel) |
| CVE-2009-3726 | CWE-476 | No (on cusp) | 7.2 | Red Hat Enterprise Linux 5,MRG (kernel) |
[1] NIST NVD rate vulnerabilities as "High" severity if they have a CVSS base score of 7.0-10.0. This ends up excluding flaws in web browsers such as Firefox which can have a maximum CVSS base score of 6.8.
[2] Red Hat Enterprise Linux 4 and 5 were also affected by this vulnerability, but with a lower CVSS base score of 4.3, due to the extra runtime pointer checking.
Back in August I found that many of the Common Vulnerability Scoring System (CVSS) scores that the National Vulnerability Database (NVD) assigned to vulnerabilities affecting open source software were incorrect.
Since then I've been sending in corrections on a monthly basis, taking into account the worst possible score across all affected platforms (and not how Red Hat products were affected specifically).
For the five months May to September 2007 I looked at 178 vulnerabilities (across all Red Hat products and services). Only 80 were accurate. Corrections were submitted to NVD and they fixed the incorrect CVSS scores on the remaining 98 vulnerabilities.
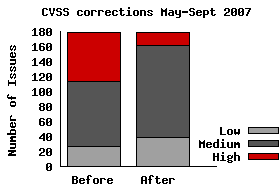
So, before the corrections, there were 65 issues rated "High" out of 178. After the corrections there are actually only 17 rated "High".
Fortunately the number of corrections needed each month seems to be decreasing, but we'll continue to send in corrections every month. Even with the corrections, the severity rating for a given vulnerability may well vary for the version each vendor ships; so you need to be careful if you are basing your risk assesments soley on the accuracy of third-party severity ratings.
The National Vulnerability Database (NVD) assign a severity rating to every vulnerability; "High", "Medium", or "Low". The rating is determined by ranges of CVSS (Common Vulnerability Scoring System) v2 scores. I've not been a big fan of CVSS: I don't think it works particularly well when applied to software that is shipped by multiple vendors, or for open source software and libraries that don't know all the possible use-cases of their software.
Even though I'm not a fan, NVD publish a CVSS score for every issue, security companies are using those scores in their vulnerability feeds to customers, and people are using them for metrics. So it's important that these scores are accurate.
I decided to take a look at how accurate the CVSS scores were, so for every vulnerability we fixed in any Red Hat product for June 2007 examined the CVSS score given by NVD. For each one figuring out if the CVSS base metrics were correct, and where they were not submitting the correction back to NVD. This analysis of the vulnerabilities was based on their possible worst-case threat to all platforms (I didn't adjust the CVSS scores for how the issues affected Red Hat products specifically).
There were 39 total vulnerabilities for which unfortunately only 8 scores were accurate. I submitted corrections to NVD and they fixed the CVSS scores on the remaining 31 vulnerabilities.
20 vulnerabilities ended up moving down in ranking, 6 vulnerabilities moved up, and 5 stayed the same (although the CVSS score changed).
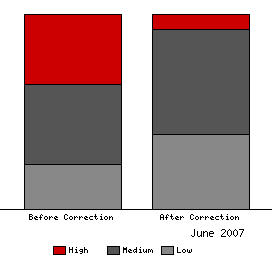
Before the corrections there were 14 issues rated "High" out of 39, after the corrections there are just 3 rated "High".
Those corrections are now live in the NVD, and I really appreciate how quick the folks behind NVD were at checking and making the changes. I've submitted to them corrections for a couple more months too, and I'll write about those when there complete. Unfortunately it does take a lot of time to investigate each issue and do the corrections, so it will limit how far back into 2007 we can correct.
The National Vulnerability Database provides a public severity rating for all CVE named vulnerabilities, "Low" "Medium" and "High", which they generate automatically based on the CVSS score their analysts calculate for each issue. I've been interested for some time to see how well those map to the severity ratings that Red Hat give to issues. We use the same ratings and methodology as Microsoft and others use, assigning "Critical" for things that have the ability to be remotely exploited automatically through "Important", "Moderate", to "Low".
Given a thundery Sunday afternoon I took the last 12 months of all possible vulnerabilities affecting Red Hat Enterprise Linux 4 (from 126 advisories across all components) from my metrics page and compared to NVD using their provided XML data files. The result broke down like this:
| Red Hat |
| ||||
| NVD |
|
So that looked okay on the surface; but the diagram above implies that all the issues Red Hat rated as Critical got mapped in NVD to High. But that's not actually the case, and when you look at the breakdown you get this result: (in number of vulnerabilities)
| NVD: High |
|
| NVD: Moderate |
|
| NVD: Low |
|
That shows nearly half of the issues that NVD rated as High actually only affected Red Hat with Moderate or Low severity. Given our policy is to fix the things that are Critical and Important the fastest (and we have a pretty impressive record for fixing critical issues), it's no wonder that recent vulnerability studies that use the NVD mapping when analysing Red Hat vulnerabilities have some significant data errors.
I wasn't actually surprised that there are so many differences: my hypothesis is that many of the errors are due to the nature of how vulnerabilities affect open source software. Take for example the Apache HTTP server. Lots of companies ship Apache in their products, but all ship different versions with different defaults on different operating systems for different architecture compiled with different compilers using different compiler options. Many Apache vulnerabilities over the years have affected different platforms in significantly different ways. We've seen an Apache vulnerability that leads to arbitrary code execution on older FreeBSD, that causes a denial of service on Windows, but that was unexploitable on Linux for example. But it has a single CVE identifier.
So if you're using a version of the Apache web server you got with your Red Hat Enterprise Linux distribution then you need to rely on Red Hat to tell you how the issue affects the version they gave you -- in the same way you rely on them to give you an update to correct the issue.
I did also spot a few instances where the CVSS score for a given vulnerability was not correctly coded. CVSS version 2 was released last week and once NVD is based on the new version I'll redo this analysis and spend more time submitting corrections to any obvious mistakes.
But in summary: for multi-vendor software the severity rating for a given vulnerability may very well be different for each vendors version. This is a level of detail that vulnerability databases such as NVD don't currently capture; so you need to be careful if you are relying on the accuracy of third party severity ratings.
